Cisco™ Anomaly Guard Module

The Cisco© Anomaly Guard Module is an integrated services module for Cisco Catalyst 6500 Series switches and Cisco 7600 Series routers that delivers a powerful and extensive solution for defending online resources against massive distributed denial-of-service (DDoS) attacks. Designed to meet the performance and scalability requirements of the largest and most demanding enterprise and service provider environments, the Cisco Anomaly Guard Module delivers unprecedented levels of protection for defeating today's increasingly complex and elusive attacks. A single Cisco Anomaly Guard Module provides the platform for processing attack traffic at multigigabit line rates. The Anomaly Guard Module employs a unique "on-demand" deployment model, diverting and scrubbing only traffic addressed to targeted devices or zones without affecting other traffic. Integrated multiple layers of defense within the Anomaly Guard Module enable it to identify and block malicious attack traffic while allowing legitimate transactions to continue flowing to their original destinations. Business operations continue uninterrupted, even in the midst of attack.
Multiple Cisco Anomaly Guard Modules, working together in a single chassis, can incrementally scale to support many times the single module rate, delivering a scalable solution that easily adapts to large and growing enterprise and service provider environments. The Anomaly Guard Module's multiprocessor architecture can support future licensed software upgrades to enhance and improve performance for defending against massive attacks.
Evolving DDoS Attacks
Today's DDoS attacks are more destructive and focused than ever. These attacks can easily elude and overwhelm the most common defenses. Composed of requests that appear legitimate, massive numbers of "zombie" sources, and spoofed identities that make it virtually impossible to identify and block these malicious flows, DDoS attacks paralyze their victims and prevent them from conducting business, costing billions of dollars per year in losses-from lost transactions and customers to damaged reputations and legal liabilities. The Cisco Anomaly Guard Module defends against all types of DDoS attacks, enabling businesses to identify and block malicious traffic without compromising their mission-critical and revenue-bearing operations. Based on a unique, patented multiverification process architecture, the Cisco Anomaly Guard Module uses advanced anomaly recognition capabilities to dynamically apply integrated source verification and antispoofing technologies in conjunction with high-performance filtering to identify and block individual attack flows while allowing legitimate transactions to pass (Figure 2). Combined with an intuitive, graphical interface and extensive multilevel monitoring and reporting designed to provide a comprehensive overview of all attack activity, the Cisco Anomaly Guard Module delivers the most comprehensive DDoS defense for protecting business operations.
How It Works
The Cisco Anomaly Guard Module is just one part of a complete detection and mitigation solution from Cisco that protects large enterprises, government agencies, hosting centers, and service providers from DDoS attacks. The Cisco Anomaly Guard Module provides a powerful, scalable solution that enables hosting and service providers to deliver valuable managed DDoS protection services to their subscribers. Working with the Cisco Traffic Anomaly Detector Module (or other third-party alerting systems that detect the presence of DDoS attacks), the Anomaly Guard Module performs the detailed per-flow-level attack analysis, identification, and mitigation services required to prevent attacks from disrupting network and data center operations. When the Cisco Traffic Anomaly Detector Module identifies a potential attack, it alerts the Cisco Anomaly Guard Module to begin dynamic diversion, which redirects traffic destined for the targeted resources-and only that traffic-for inspection and scrubbing. All other traffic continues to flow directly to its intended destination, delivering a low-impact, highly reliable, and economical solution that offers easy installation. Diverted traffic is rerouted through the Cisco Anomaly Guard Module, where it is subjected to multiple layers of scrutiny to identify and separate "bad" flows from legitimate transactions. Specific attack packets are identified and removed, while "good" traffic is forwarded to its original destination, helping to ensure that real users and real transactions always get through, and providing maximum availability. Cisco Anomaly Guard Module Benefits.
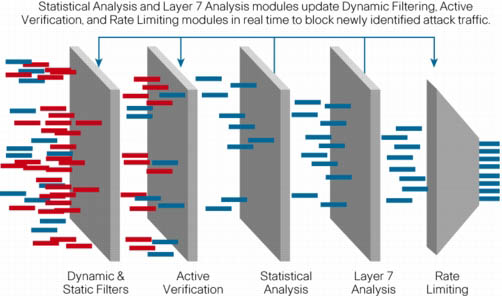
Multistage Verification
The Cisco Anomaly Guard Module's innovative blocking techniques are based on Cisco's unique multiverification process architecture, which delivers multiple interactive layers of defense to identify and block all types of attacks with unparalleled accuracy. Integrated dynamic filtering and active verification technologies, driven by a sophisticated profile-based anomaly recognition engine, enable rapid, automatic protection against all types of assault-even day-zero attacks. The Anomaly Guard Module performs detailed per-flow analysis and blocking to stop attack traffic with surgical precision, while allowing legitimate transactions to flow freely. The anomaly recognition engine uses a baseline of normal behavior that includes thorough per-flow profiles to define the normal or expected behavior specific to each protected resource. If desired, users may enhance highly accurate default profiles with automatic site-specific learning that customizes the profile for individual devices or zones. An additional rate-limiting feature provides a mitigation alternative to blocking, as well as protection against flash floods. Static filters, comprehensive Flex filters based on the Berkeley Packet Filter that allow the creation of a deep packet inspection filter, and bypass "whitelist" filters are also available. The Cisco Anomaly Guard Module also features "zombie killer" capabilities that defeat all types and sizes of attacks, including those launched by compromised computers known as zombies-one of the most prevalent and difficult-to-stop DDoS attack sources today. When deployed in a clustered configuration, Anomaly Guard Modules can identify and block literally hundreds of thousands of individual zombies, delivering unparalleled levels of protection for defeating the largest botnet attacks.
Multigigabit Performance
The Cisco Anomaly Guard Module features dedicated network processors that support attack analysis and cleaning at full gigabit line rates, defending against large-scale DDoS attacks, including those launched by massively distributed attackers such as compromised zombie hosts. With Cisco Anomaly Guard Module Software Release 5.1 or lower, each module has a performance of 1 Gbps throughput. In Release 6.0, the Cisco Anomaly Guard Module will be able to operate at 3 Gbps throughput. The higher performance is achieved by turning up additional network processors on the module and can be enabled using a software license. Multiple Cisco Anomaly Guard Modules can be installed in a single chassis to provide incremental scaling of both packet-per-second rates and zombie defense capacities-sufficient for protecting even the largest enterprise and service provider environments against the most serious threats. These multiple modules can also be clustered to protect a single resource or zone without requiring special load balancers.
Scaling to 10-Gigabit Plus Capacity
With Cisco Anomaly Guard Module Software Release 6.0, since each Cisco Anomaly Guard Module can operate at 3 Gpbs, 10 gigabits plus performance can be achieved by clustering up to four modules in a single chassis. See the performance metrics table below for more information.
Dynamic Diversion
The Cisco Anomaly Guard Module employs a powerful on-demand scrubbing model. It is not inserted into the normal data path like traditional inline devices; rather, it uses dynamic diversion to automatically redirect traffic addressed to specific resources or zones under attack-and only that traffic-for further scrubbing. When an attack is suspected, the Anomaly Guard Module uses the Cisco Route Health Injection (RHI) protocol to insert a routing update into the supervisor engine routing tables to make the Anomaly Guard Module the next hop for any traffic destined for the targeted resource. Once the traffic destined for the targeted device or zone has been cleaned and malicious packets blocked, legitimate transactions are forwarded on to their original destinations, helping to ensure that no critical requests are lost. By limiting diverted traffic to only those flows addressed to resources or zones currently under attack, the Cisco Anomaly Guard Module provides optimal resource utilization, transparency, and reliability for a scalable solution that can meet the needs of the largest enterprise and service provider environments. This Layer 3 insertion also enables simplified and low impact installation, as well as ease of operational maintenance and troubleshooting.
Multilevel Monitoring and Reporting
The Cisco Anomaly Guard Module features an intuitive, Web-based GUI that simplifies the policy definition, operational monitoring, and report generation processes. Multiple monitoring and reporting levels provide network operators, security administrators, and clients with detailed real-time and historical information (Figure 5). Attack reports provide details for individual attacks, including characteristics, lists of identified zombies, and specific enforcement actions used, enabling security experts to review and tune the Cisco Anomaly Guard Module security policies. Meanwhile, customer-level historical summaries enable service providers to easily report on successful protection against the variety, duration, and scale of attacks. In addition, an interactive mode allows users to review and approve recommended actions and policies prior to activation, providing manual control over attack responses, if desired.
